Debugging Sensors
One of the main components of hwdbg is debugging sensors. This section discusses the debugging sensors implemented in the debugger.
Sensors in Hardware Debugging
Sensors play an important role in hardware debugging by providing real-time data about the internal state and environmental conditions of hardware systems. They enable precise monitoring and control, helping hardware engineers to identify issues, optimize performance, analyze side-channel attacks, and ensure reliability. In this section various types of sensors are explored that are used in hardware debugging, including their functionalities, applications, and integration into hwdbg.
Side-channel Attacks in Microchips/IP Cores
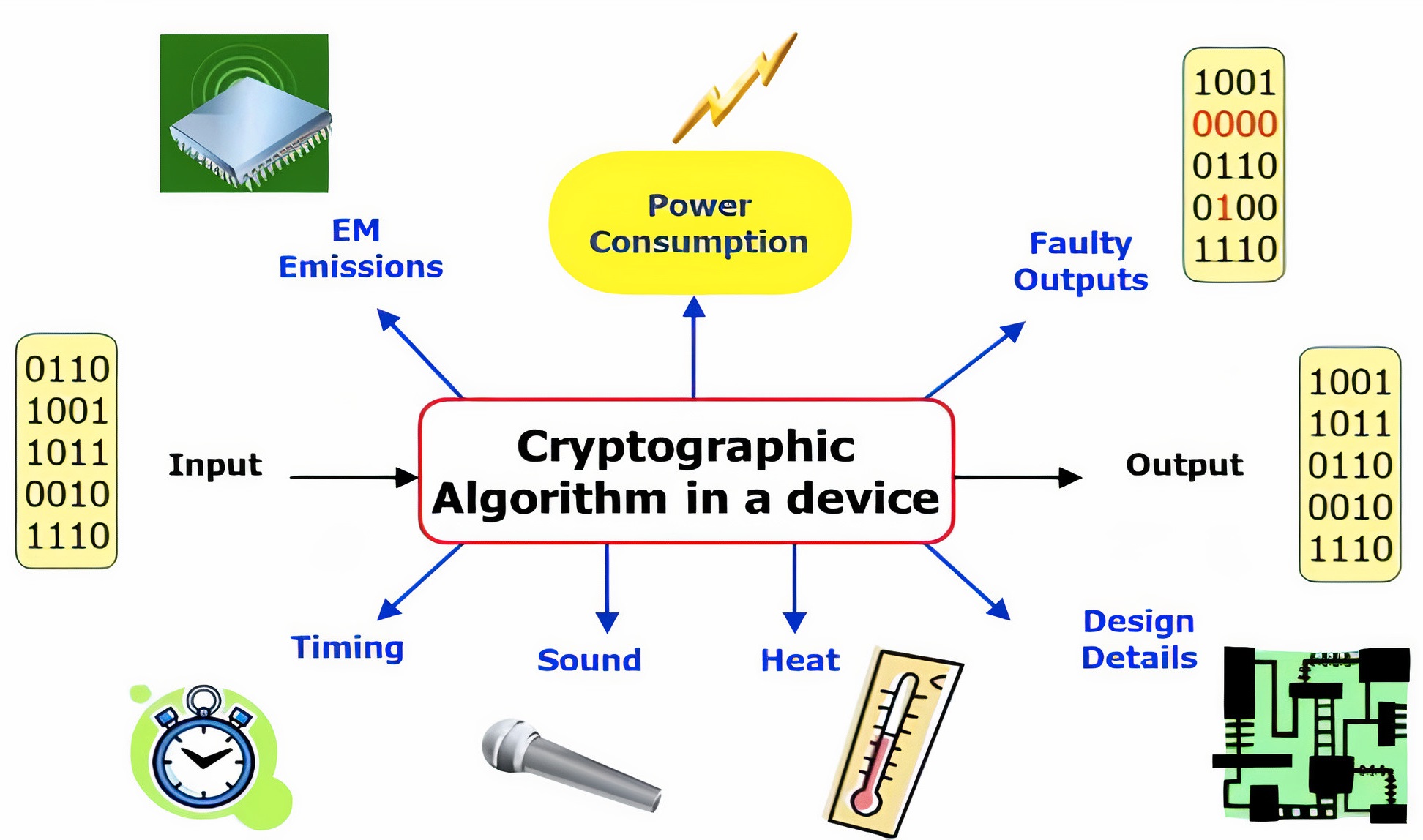
Hardware side-channel attacks exploit the physical characteristics of microchips and IP cores to extract sensitive information without directly interacting with the system's primary data channels. In these cases, sensors play a key role in facilitating these attacks by providing access and creating data based on characteristics like power consumption, electromagnetic emissions, temperature, and timing, which correlate with specific operations or data being processed. For example, voltage and power sensors can monitor fluctuations in power consumption, which can be analyzed through techniques such as Differential Power Analysis (DPA) to reveal cryptographic keys and other confidential data. Temperature sensors can detect thermal variations caused by different processing states, enabling thermal imaging attacks that indirectly uncover sensitive information.
Time-to-digital converters (TDCs) and frequency sensors can capture high-resolution timing information, allowing attackers to perform timing analysis attacks that exploit the time differences in processing operations to infer secret data. Ring oscillators (RO) can detect minute variations in signal delays caused by different computational activities, facilitating delay-based attacks. Clock sensors can monitor the integrity of clock signals and detect anomalies caused by tampering or glitching attacks aimed at disrupting normal operations to extract sensitive information. By leveraging these sensors, attackers gain access to a wealth of side-channel data that can be analyzed to compromise the security of microchips and IP cores.
As a main component, hwdbg implements these sensors to provide facilities for hardware engineers and security researchers to analyze microchips and IP cores.
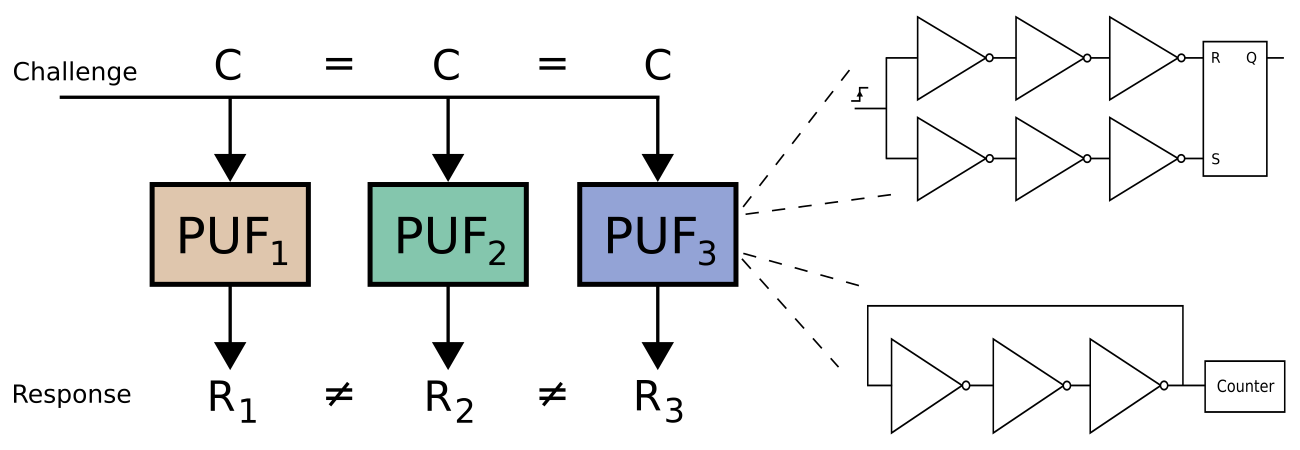
Physical Unclonable Function (PUF)
A Physical Unclonable Function (PUF) is a physical entity embodied in a physical structure and usually utilized in microchips and other electronic devices to generate unique, device-specific cryptographic keys based on the inherent and uncontrollable physical variations that occur during the manufacturing process. These unique differences, such as variations in silicon pathways, ensure that each PUF is unique and make it theoretically impossible to duplicate or clone. PUFs provide a robust method for secure authentication and encryption, as the unique response generated by a PUF can be used to verify the identity of a device. Figure below illustrates a simple design of a Ring Oscillator (RO) which is a variant of a PUF device.
Comparative Analysis of Sensors
Comparing different sensors involves evaluating performance metrics such as accuracy, resolution, power consumption, response time, and operating range. Each sensor type has its strengths and weaknesses, making them suitable for different applications.
The suitability of each sensor type depends on the specific requirements of the debugging task. For example, TDCs are ideal for high-precision timing measurements, while voltage sensors are essential for power management and stability.
Common challenges in sensor integration include calibration, environmental compensation, power efficiency, and data interpretation.
A combination of results gathered from these sensors can be used to determine the internal state of the debuggee, providing security researchers and hardware engineers with meaningful data to interpret the internal conditions of the target device or IP core.